What is VPN (Virtual Private Network)? How it Works?
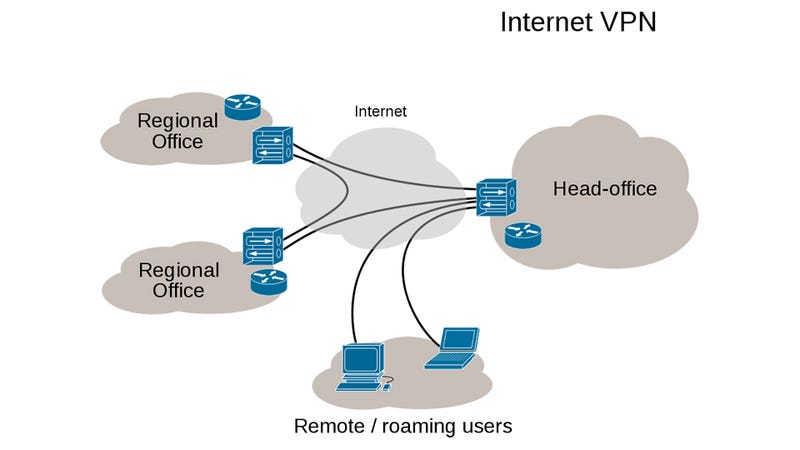
 Short Bytes: VPN is a technology used to setup a private network over the internet to share the resources of a corporate intranet with remote users and other office locations of the company.
Short Bytes: VPN is a technology used to setup a private network over the internet to share the resources of a corporate intranet with remote users and other office locations of the company.
irtual Private Network or simply VPN is a personal network created over the internet, so that the devices connected over it can have an uninterrupted communication, regardless of any physical or digital barriers in the mid-way.
Writing is a good habit, if you use your creative mind and write some good stuff, it would make you sound more intelligent among your friends. So, don’t wait, just use your keyboard and type your imagination in the comments section below.
How it works?
The working of VPN is not a tough deal to understand, though it is. But, before that, you need to get an idea about the protocols or set of rules in laymen terms, used by VPN in providing a secure personal network. Let’s tell you more about it:
SSL (Secured Socket Layer): It uses a 3-way handshake method for assuring proper authentication between the client and server machines. The authentication process is based on cryptography where certificates behaving as cryptographic keys already stored in the client and server, are used for initiating the connection.
IPSec (IP Security): This protocol can work on transport mode or tunnelling mode, so that it can do its job of securing the VPN connection. The difference between the two is, transport mode only encrypts the Payload in the data i.e. only the message present in the data, whereas tunnelling mode encrypts the whole data to be transmitted.
PPTP (Point-To-Point Transfer Protocol): It connects a user located at some remote location to a private server in a VPN network, and also uses the tunnelling mode for its operations. Its low maintenance and simple working makes it the most widely adopted VPN protocol, further credit goes to the inbuilt support provided by Microsoft Windows.
L2TP (Layer Two Tunnelling Protocol): It facilitates the tunnelling of data between two geographical sites over the VPN network, often used in combination with the IPSec protocol which further aids to the security layer of the communication.
So, you have a rough idea about the various protocols used in a VPN. We shall proceed further and see how it works. When you are connected to a public network such as internet, you can assume that all your data is flowing through a big tunnel along with the data of other users.
So, anyone who wants to spy on you, can easily sniff your data packets from the network. When VPN comes into the scene, it actually provides you a personal tunnel inside that big tunnel. And all your data is transformed into garbage values, so no one can recognize it.
Setting up a VPN Connection involves Three Phases:
Authentication: In this phase, data packets are first encapsulated, basically wrapped inside another packet and some headers and other stuff are attached, all done to conceal the identity of the data packets. Now, your device initiates the connection by sending a Hello request to the VPN server, which replies with an acknowledgement and asks for the user credentials to clarify the authenticity of the user.
Tunnelling: After the authentication phase is finished, what we say, an imaginary tunnel is created which provides a direct point to point connection through the internet. We can send whatever data we want to via that tunnel.
Encryption: After we’ve successfully created the tunnel, we can send whatever information we want to, but that information is still not safe if we are connected to a free VPN service, which is also used by other people. So, we encrypt the data packets before sending them over the tunnel, thus barring any other user to peep into our packets, as he will only see some unrecognisable rubbish data flowing through the tunnel.
Say, you want to access a website, your device will send the access request to the VPN server which will then forward the request to the website in its name and receive the data from it. This data will then be transferred back to your device. And the website will think, the VPN server is the user and will find no trace of your device as the actual user.
Uses of VPN:

Remote User Access: A VPN connection is used to provide direct access of a corporate network to a user who is not in the geographical coverage of the corporate network. Logically, the remote user is connected just like a normal user who is using the network within the corporate premises.
Site to Site: VPN is also used to provide a homogenous network environment to a corporate firm having its office locations in different parts of the world. Thus, creating an uninterrupted sharing of resources bypassing the geographical hurdles.
Other uses include, accessing those services on the internet which are not available in a particular country or region, accessing censored content or if a user simply wants to remain anonymous on the internet.
Pros and Cons:
The biggest advantage of using a VPN is the cost effectiveness it facilitates in providing a single private network in comparison to using separate leased lines which can burn the pockets of corporate firms. All credited goes to the internet, for acting as the medium for uninterrupted VPN connections.
Apart from all the good things VPN does for us, it has its weak sides too. Not having a streamlined procedure for ensuring Quality of Service (QoS) over the internet, is the biggest incapacity VPN technology has in its possession. Furthermore, the level of security and authenticity outside the private network is beyond the purview of VPN technology. The incompatibility between different vendors only adds to its bunch of drawbacks.
Popular VPN services:
HideMyAss, PureVPN, VyprVPN, all these are well known the QoS and security they provide in their VPN connections.
Cyber Ghost, Surf Easy, Tunnel Bear are some free VPN services you can use if you don’t want to shell out your pocket. But you’ll have to satisfy yourself with less features, download limits, or advertisements. Also, these free services can’t beat the paid services, note that.
VPN on Android:
You can also setup a VPN connection on your smartphones running on Android OS. This allows you to access your company’s private network right on your Android Devices. VPN also facilitates the network administrator to control your device, add or delete data and track your usage.
Winding Up:
VPN has so far equipped us with an extraordinary level of security and anonymity we can accomplish while sharing our confidential data over the internet. Corporate giants have always admired the ease and uniformity they can engineer in their network while using VPN. Though, it has its limitations, but so far it has outperformed our expectations and should be praised for the cost effectiveness it provides in its operations.
Have a look at this video about VPN:
Writing is a good habit, if you use your creative mind and write some good stuff, it would make you sound more intelligent among your friends. So, don’t wait, just use your keyboard and type your imagination in the comments section below.

No comments:
Post a Comment